 The days of smugness of Apple Macintosh users are coming to an end. Symantec is reporting that they’ve recently identified a virus for Macs. It’s a pretty rare occurrence, given there’s only been about 10 Apple viruses in the last 10 years.
The days of smugness of Apple Macintosh users are coming to an end. Symantec is reporting that they’ve recently identified a virus for Macs. It’s a pretty rare occurrence, given there’s only been about 10 Apple viruses in the last 10 years.
Given the rareness of this, we felt it’d be worth delving further into this one.
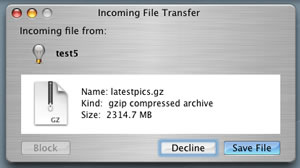
The OSX/Leap-A virus uses the Apple Instant Messaging (IM) software, iChat, to spread itself. Once installed, it spreads itself by forwarding the virus payload (translated – reads the program that infects your machine) as photos from your IM pal, under the name ‘latestpics.tgz’. It’s not selective, it just runs through your IM list attempting to infecting each of them in turn.
Macs still safer
The next stage illustrates PC & Mac virus are notably different. To become infected, the recipient has to get involved, and not just once, but follow a few clicks.
In the case of the OSX/Leap virus – the .gz file has to be accepted; clicked on to unbundle; then executed. The more steps there are to follow, leads to a significant reduction in the chances of it being executed without suspicion. PC viruses often install themselves without the user knowing anything about it.
Symantec tell us that to date, no Apple Mac virus has been able to install itself without the user getting involved in some way.
Spotlight – used by OSX/Leap
Illustrating the double-edged side of all technology, this virus uses Spotlight, the Apple supplied quick searching service that ships with OSX.
 By identifying the four most recently executed apps using Spotlight, it uses this information to attempt to infect these files.
By identifying the four most recently executed apps using Spotlight, it uses this information to attempt to infect these files.
Many Mac users will find this the most disturbing aspect of this virus. Something as integrated and wide-ranging as Spotlight being able to be taken over by a malicious program is very worrying.
Safe with Intel-based Mac?
(Update: Thanks to Lee Dickey for getting in touch pointing out that what we’ve written, about OSX.Leap not running on Intel-Macs conflicts with the advice on the Symantec page. To be clear, when we were researching the original article we spoke to Eric Chien, Chief Researcher at Symantec. He told us it did _not_ run on the Intel-Macs.)
(Update 2: We’ve re-contacted Mr Chien today, and he now informs us that it _does_ run on Intel-Macs, but won’t spread from them. His words …
There is no malicious payload (e.g., deleting of files, sending out personal information, etc.) in the threat itself and thus, on both Intel AND PPC.
The threat merely tries to replicate. On Intel, it does not executeproperly and does not replicate successfully, but can be saved andcopied onto the system. The threat itself was clearly written for PPC.
Ammendmants to our text have been made.)
When delving into this, we found it interesting that the virus code doesn’t execute, at all, spread on Intel-based Macs, even when using the compatibility emulator, Rosetta. Summary – Intel-based Macs are safe from damage this heartless-beasty.
Start the queue here marked ‘Conspiracy: Getting you to buy an Intel-based Mac.’
Discussion on IM worm viruses
We chatted over the currently state of Apple Mac viruses with Eric Chien, Chief Researcher with Symantec. It’s clear that it’s early days for Mac viruses, just take a look at the total lack of social engineering involved with the virus payload. All that’s delivered is the gz file, no supporting message to entice you into looking at them like, ‘hey have a look at these’, ‘here’s some shots of you last time you danced naked through town’, nothing.
On the general subject of IM worms (viruses that use IM to transport themselves), we wondered if IM is less successful as IM users are generally more tech-aware, therefore less likely to be tricked into getting infected. As Chien pointed out, there’s also an instant response route to the potential-infector – ‘what’s this latestpics.tz you’re sending me’ – which is likely to de-rail a lot of infection.
One of the benefits in using IM to distribute viruses is that it plays on the intimate relationship with everyone on your IM list. They wouldn’t be there without that level of trust and this is easily abused – currently.
Full details of how OSX/Leap installs itself and how to get rid of it are available from Symantec