 Much as we hate steenkin’ virus writers, we have to reluctantly take our hats off to the author of this Yahoo! Messenger Worm for at least being a bit original.
Much as we hate steenkin’ virus writers, we have to reluctantly take our hats off to the author of this Yahoo! Messenger Worm for at least being a bit original.
Described as “one of oddest and more insidious pieces of malware we have encountered in years,” by Tyler Wells, senior director of research at FaceTime Security Labs, the ‘yhoo32.explr’ Instant Messaging worm takes the novel step of installing its own Web browser onto a victim’s PC.
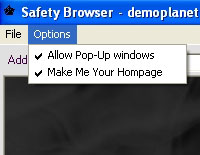
Somehow managing to keep a straight face, the dodgy-as-feck application announces itself as “The Safety Browser”, and sneakily uses the IE icon to make it easy for users to mistake it for the legitimate Internet Explorer browser.
 Once installed, the browser opens up a user’s PC to a world of nasties, switching on pop-ups by default, hijacking their Internet Explorer homepage to point to a well-iffy site stuffed full of spyware-loaded links and, curiously, introducing an awful looped music track that plays every time the computer is turned on.
Once installed, the browser opens up a user’s PC to a world of nasties, switching on pop-ups by default, hijacking their Internet Explorer homepage to point to a well-iffy site stuffed full of spyware-loaded links and, curiously, introducing an awful looped music track that plays every time the computer is turned on.
Once installed on the victim’s machine, the self-propagating worm hotfoots it to the user’s Yahoo! Messenger contacts and sends out links to a Website that then loads a command file onto the user’s PC and installs the (ahem) ‘Safety Browser’.
 “This is the first instance of a complete Web browser hijack without the user’s awareness,” said Tyler Wells.
“This is the first instance of a complete Web browser hijack without the user’s awareness,” said Tyler Wells.
“Similar ‘rogue’ browsers, such as ‘Yapbrowser,’ have demonstrated the potential for serious damage by directing end-users to potentially illegal or illicit material,” he added, before concluding that such ‘rogue’ browsers are becoming the “hot new thing among hackers.”
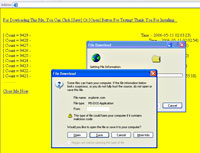 The worm was found by the India research arm of FaceTime Security Labs via a ‘honeypot’ a trap set to detect viruses, worms, spyware and other threats, and reflects the growing threat from Instant Messenger applications and protocols being used to distribute malicious files and executables, as well as IM spamming (which now has now earned the daft acronym ‘SPIM’).
The worm was found by the India research arm of FaceTime Security Labs via a ‘honeypot’ a trap set to detect viruses, worms, spyware and other threats, and reflects the growing threat from Instant Messenger applications and protocols being used to distribute malicious files and executables, as well as IM spamming (which now has now earned the daft acronym ‘SPIM’).
If you want to find out more about the details of this latest worm – and the people behind it – check out the amusing blog of Chris Boyd, a FaceTime Security Labs researcher.